What is CVE-2024-6387?
CVE-2024-6387, dubbed “regreSSHion,” is a severe vulnerability in OpenSSH that allows remote code execution with root privileges. This vulnerability is a regression of CVE-2006-5051, reintroduced in OpenSSH 8.5p1 and present until 9.7p1.
Status and Discovery
Impact and Risk Assessment
The severity of CVE-2024-6387 lies in its potential to:
- Compromise Entire Systems: Attackers can install malware, steal data, and disrupt services.
- Bypass Authentication: Unauthorized access to systems is possible.
- Remote Code Execution: Attackers can execute arbitrary code with root privileges.
Affected Versions and Operating Systems
- OpenSSH Versions: 8.5p1 to 9.7p1
- Operating Systems: Unix-like systems, including Ubuntu, Debian, Fedora, CentOS, and BSD variants.
Exploitation Scenario
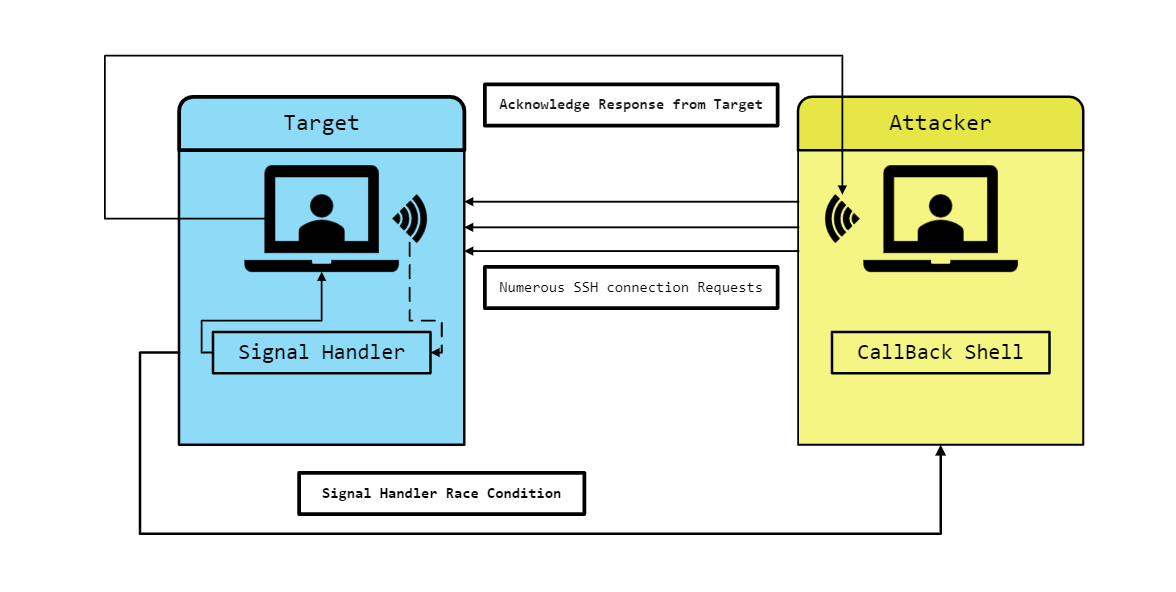
Overview
An attacker can remotely exploit a vulnerability in OpenSSH by sending specially crafted packets to the server. This exploitation is possible without any authentication, making it highly risky as it allows for remote code execution with root access.
Steps in the Exploitation
Identification:
- The attacker identifies a target system running a vulnerable version of OpenSSH.
Crafting Malicious Packets:
- The attacker crafts specific packets designed to exploit the race condition in the OpenSSH signal handler.
Sending Packets:
- The attacker sends these crafted packets to the OpenSSH server. These packets are designed to manipulate the timing of the signal handler, causing it to mishandle memory or other resources.
Triggering the Vulnerability:
- By repeatedly sending these crafted packets, the attacker triggers the race condition, leading to memory corruption or other unexpected behaviors in the OpenSSH process.
Gaining Access:
- Successful exploitation of the vulnerability allows the attacker to execute arbitrary code on the server. Since the vulnerability permits unauthenticated access, the attacker can gain root privileges.
Post-Exploitation:
- With root access, the attacker can perform various malicious actions, such as installing backdoors, stealing sensitive data, or further compromising the network.
Mitigation
- Update OpenSSH: Apply the latest patches from OpenSSH.
- Configure SSHD: Set
LoginGraceTimeto 0 in/etc/ssh/sshd_configto mitigate the vulnerability (at the cost of potential denial-of-service from MaxStartups exhaustion). - Network Security: Use firewalls and intrusion detection systems.
Detailed Steps for Applying SSHD Configuration
Open a terminal and execute the following command:
echo "LoginGraceTime 0" | sudo tee /etc/ssh/sshd_config.d/cve-2024-6387.confReload the SSH service to apply the changes:
sudo systemctl reload ssh.service
Additional Context and Developments
Rigorous Security Process
OpenSSH is developed with the same rigorous security process that the OpenBSD group is famous for. To report a security issue, contact the private developers list at [email protected]. More information is available on the OpenBSD security page.
Race Condition in SIGALRM Handling Code
The issue stems from a race condition in the sshd(8) signal management code. This can lead to remote code execution on non-OpenBSD systems. Disabling the login grace timeout (LoginGraceTime=0 in sshd_config) can prevent this attack but makes denial-of-service attacks easier.
Logic Error in ObscureKeystrokeTiming Option
Another related issue affects OpenSSH versions 9.5p1 to 9.7p1, where a logic error in the ObscureKeystrokeTiming option exposes limited keystroke timing information. Disabling this feature (ObscureKeystrokeTiming=no) can avoid this issue.
Key Takeaways
- Critical Threat: Unauthenticated remote code execution with root privileges.
- Wide Impact: Affects numerous Unix-like operating systems.
- Urgent Mitigation: Update OpenSSH and configure security settings.
Conclusion
CVE-2024-6387 is a critical vulnerability that underscores the importance of keeping systems updated and implementing robust security measures. Immediate action to update OpenSSH and enhance network security is crucial to protect against this threat. For more detailed information, refer to the Ubuntu Security Notice and other relevant resources.
- Stay informed and proactive to defend against threats like CVE-2024-6387. For more details, refer to the Qualys Security Advisory and the official CVE Record.
