The Form-Grabbing Frenzy: How Cybercriminals Are Exploiting Thread Injection in 2024
2024 has seen a surge in sophisticated cyberattacks, with form-grabber malware using thread injection techniques to steal sensitive information becoming alarmingly common. Among these, the notorious FormBook malware stands out, having resurfaced in a series of global phishing campaigns.

FormBook’s Resurgence
Originally discovered in 2016, FormBook is a data-stealing trojan that has been frequently used by cybercriminals due to its powerful capabilities and ease of use. This year, it has made a dramatic comeback, spreading through malicious emails designed to deceive even the most vigilant users. These phishing emails often masquerade as legitimate business communications, such as requests to verify invoice details, luring victims into downloading and opening malicious attachments Bitdefender.
The Mechanics of Thread Injection
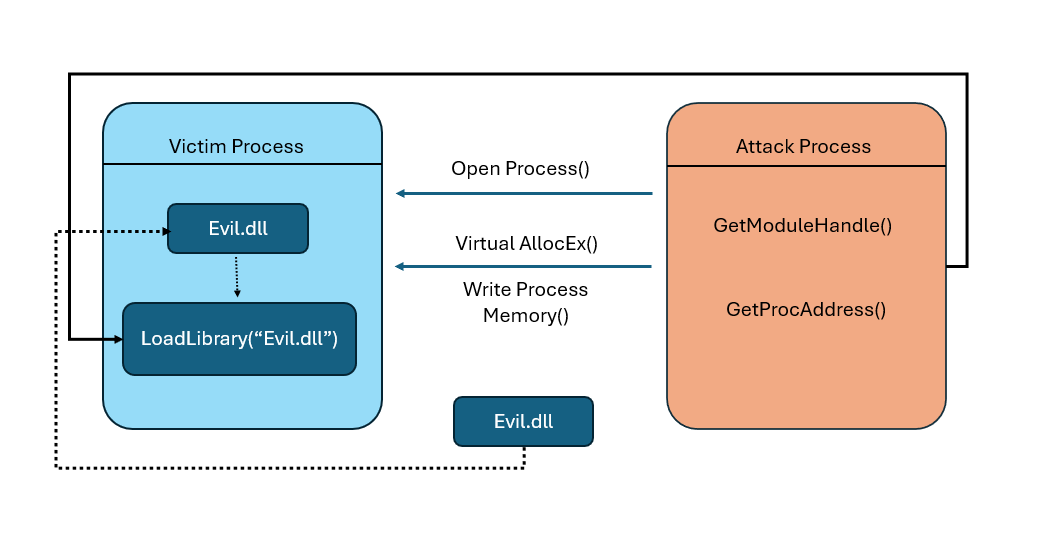
Thread injection is a stealthy technique that allows malware like FormBook to insert its code into the process of another application, typically a web browser such as Internet Explorer. This method involves several steps:
- Infection: The victim’s PC is initially infected through a phishing email containing a malicious attachment.
- Code Injection: The malware injects its code into the browser process. Techniques like DLL injection, process hollowing, and code cave injection are used to embed the malicious code.
- API Hooking: The injected malware hooks into specific API functions responsible for handling web form data, intercepting it before it is encrypted and sent over the internet.
- Data Exfiltration: The stolen data, which includes usernames, passwords, and financial information, is then sent to the attacker’s server, often using encrypted channels to evade detection Stormshield.
Real-World Impact
Recent analyses have shown how FormBook leverages these techniques to evade security measures. By dynamically importing functions and employing anti-debugging tricks, it can bypass traditional security solutions. This makes it a particularly dangerous threat, capable of stealing a vast amount of sensitive information from unsuspecting victims Stormshield Bitdefender.
Staying Safe
With the increasing sophistication of threats like FormBook, it is more important than ever to take proactive steps to protect your data:
- Keep Software Updated: Regularly update your operating system, browsers, and security software to patch known vulnerabilities.
- Use Comprehensive Security Solutions: Employ antivirus and anti-malware programs that offer real-time protection and advanced threat detection capabilities.
- Be Cautious with Emails: Always verify the origin and legitimacy of emails, especially those with attachments or links, before opening them.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security, making it harder for attackers to access your accounts even if they obtain your credentials.
Conclusion
The re-emergence of FormBook in 2024 underscores the evolving nature of cyber threats. By understanding the mechanics of form-grabber thread injection and staying vigilant, individuals and organizations can better protect themselves against these insidious attacks. Stay informed, stay updated, and always be cautious with your online interactions to keep your data safe from prying eyes.
